
Industry Q&A with NaWAS Anti-DDoS
1.What kind of threats are you seeing in DDoS attacks today?
The main threats we see today are DNS and NTP amplification attacks. These are UDP-based, and use open resolvers to flood a server or network with an amplified amount of traffic rendering the server and surrounding infrastructure inaccessible.
Overall, there has been a decline in DDoS attacks so far in 2022 compared to 2021. However, looking back further, we see that the first three quarters of this year already saw more DDoS attacks than the whole of 2020.
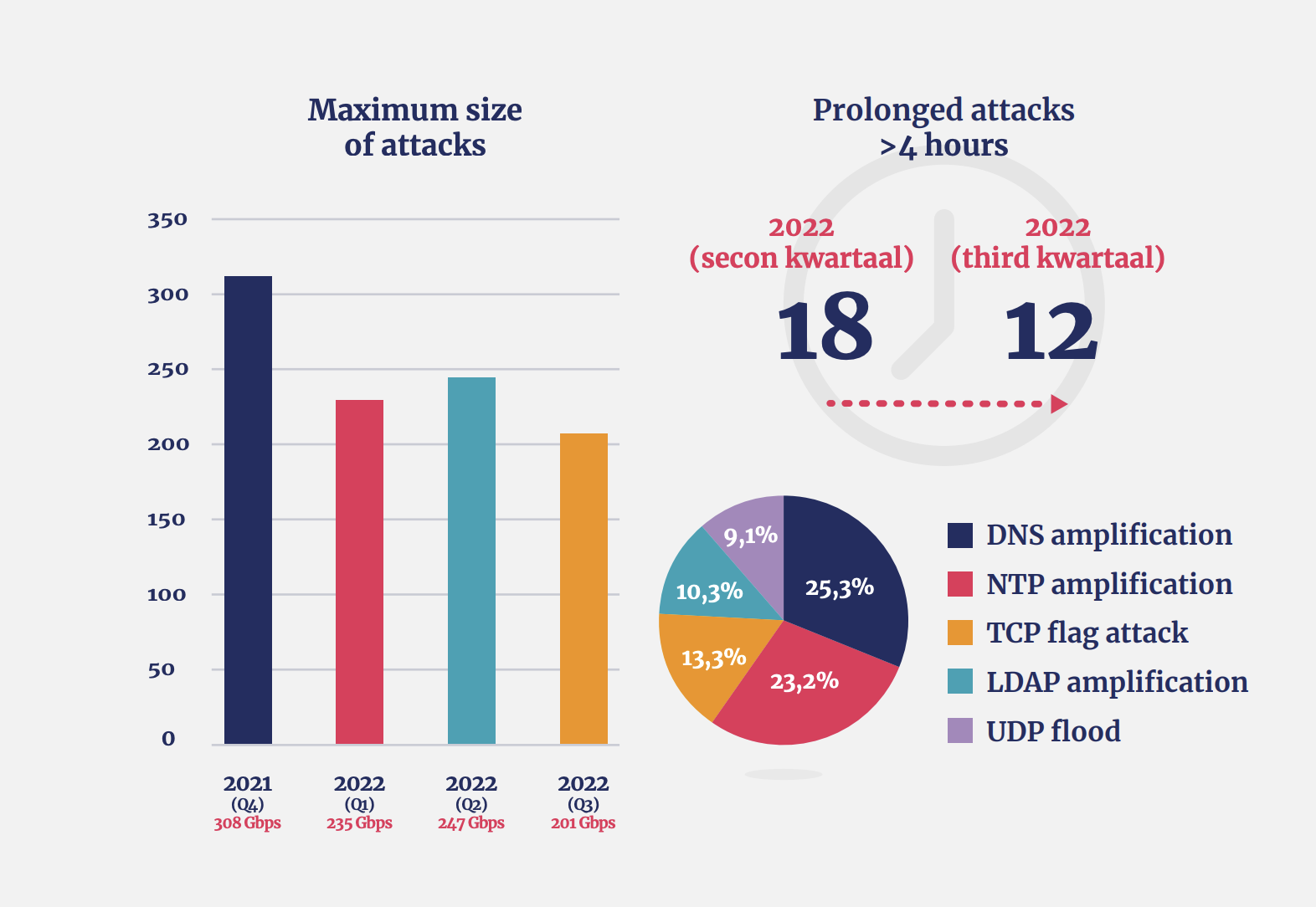
Figure 1: Types of DDoS attack and maximum attack sizes 2021-2022. Source: The Dutch National Scrubbing Center (NaWas). Original version available here.
2. What is NaWAS?
NaWAS has been running since 2013 and is the Dutch Scrubbing Center, which means we are focused on the most efficient ways of protecting our members, both in the Netherlands and abroad, from DDoS attacks. NaWAS is part of NBIP, which is a Dutch association of ISPs and Voice-over-IP providers focused on dealing with common problems affecting our industry. NaWAS is a not-for-profit and community based concept with the aim of offering a high-quality service while keeping fees as low as possible. We are based in the Netherlands but have members all across Europe.
3. How does NaWAS work to protect networks?
Our core focus is to protect our members from DDoS attacks and to ensure that only clean traffic reaches their networks. To do this, we run multiple mitigation devices in line each with its own set of mitigation rules. So we use prefix filtering, volumetric protection (which protects you from the kind of amplification attacks we mentioned earlier), and L7 detection which uses highly specialised forms of intelligence and analysis. The goal is to stop DDoS traffic before it gets to our members’ networks.
We work in an advisory role to help our members with detection tools. On the reporting side, we share all attack data in our member portal and publish a public, quarterly report where we highlight trends. We are also very active working with university projects focused on DDoS mitigation and research.
4. Why is it so important for NaWAS to be connected to Internet Exchanges (IXes) like Netnod?
Connecting to IXes like Netnod is vital for us. Having fast, direct interconnectivity with our members over an IX means we can deliver clean traffic to them with low latency in a way that easily scales as our membership base grows. Connecting to Netnod means we can reach all Nordic-based networks and send them clean traffic over a private VLAN. We don’t have to set up infrastructure across the Nordics as we can trust Netnod’s platform to deliver traffic to our members.
5. What are your top 3 tips for networks looking for anti-DDoS strategies?
- DDoS protection is a necessity, not a luxury. It’s like fire insurance
- Aim for redundancy if possible, e.g an on-prem solution and a mitigation provider like NaWAS
- You need to balance:
- flexibility (what can the service provide, does it only cover large prefixes?);
- redundancy (what failover do you have if one level of DDoS protections fails?);
- and cost-effectiveness (how can you get the most for your money, where are the CAPEX/OPEX costs?)
You can read more about NaWAS here.
Frank Dupker
Frank has 25 years of experience in IT building businesses in Security. Over the last 5 years, he has focused on growing NaWas anti-DDoS services in the not-for-profit ISP community in Europe and fighting DDoS outside of Europe.

